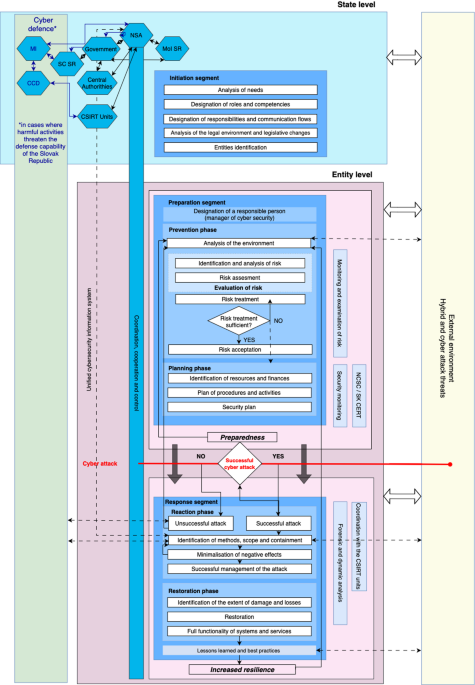
As part of the research and in-depth analysis, a cyber resilience model was developed. The model is based on the implementation of new normative acts of cybersecurity into existing crisis management frameworks. The list of normative acts used is provided in Table 1.
The model has the ambition to contribute to increasing the level of cyber resilience by implementing new EU legal acts in the field of cyber security in the national environment. The model is presented as Fig. 1. The initiation segment of the model assesses the fundamental requirements for implementation, including competences, responsibilities, and communication flows. It also prepares the necessary legislative adjustments and identifies key actors within the Slovak Republic, subsequently grouping them based on their roles.
The preparation segment is the heart of the cyber resilience model. From a crisis management perspective, two key phases are included in this segment, prevention phase and the planning phase. Once the processes and activities in the preparedness segment have been implemented, the model assumes that the desired level of preparedness, which is an integral part of the resilience, has been achieved.
The response segment is activated by a cyber-security incident, as defined by relevant Slovak legislation. If the attack is successfully repelled, lessons learned and good practices are communicated to the preparation segment, specifically to the prevention phase, analysis of the environment. This is one of the ways in which crisis management cycle is completed and subsequently a new one initiated. If the cyber-attack has been successful, it moves into the implementation of the response segment to the reaction phase and then the restoration phase. The outcome following the successful execution of the response segment is an increase in the entity’s resilience.
State level
At the state level, public authorities are dealing with cyber security and cyber defence. In the field of cybersecurity, the NSA performs the main coordinating function. It cooperates with the Government of the Slovak Republic and other central authorities. The Ministry of Interior (MoI) is explicitly mentioned in the model, as the model uses the implementation of the NIS2 Directive as an example. The Directive specifies that essential entities include critical infrastructure elements, where the coordination role is performed by the MoI. Critical infrastructure elements could be excluded into a separate category in the case of the Slovak Republic, but this would require a change in the law. CSIRT units have a special role. Together, these bodies carry out coordination and control activities in relation to the involved entities.
Given its competences, the NSA also deals with most cyber-attacks. However, if an attack could threaten the defence, defence capability or security of the Slovak Republic, the Military Intelligence (MI), which is responsible for the cyber defence of the country, intervenes the process in accordance with Act No. 500/2022 Coll. on Military Intelligence12.
The Centre for Cyber Defence of the Slovak Republic (CCD) is a special organisational component of the Military Intelligence, which performs tasks in the field of national defence in cyberspace. It communicates with CSIRT units and via the MI with the NSA when necessary.
The competences of the NSA and MoI are clearly defined, while the Security Council of the Slovak Republic (SC SR) serves as the primary decision-making body overseeing related activities. In the model, the Security Council is strategically positioned to reflect its role in both peacetime and in situations involving threats to national defense, security, or defense capabilities.
On the right side of the model, the external environment is depicted as a source of both hybrid threats and cyber-attacks. Continuous interaction with this environment occurs at both the state and entity levels, particularly within the preparation and response segments of the model.
The initiation segment is designed to prepare the conditions for the implementation of new normative acts on cybersecurity as well as new normative acts on hybrid threats into existing crisis management frameworks. The implementation of the NIS2 Directive has been chosen as an example. This segment is crucial because it creates the conditions for the effective implementation and enforcement of new normative acts. Within the segment, the basic needs for implementation are analysed, competences, responsibilities and communication flows are established, the necessary legislative changes are prepared, and finally key and important actors are identified and then grouped.
The model links cybersecurity with critical infrastructure security, considering the structure of the security system of the Slovak Republic. Critical infrastructure elements are considered as key actors in the model, as in the NIS2 Directive. The cooperation between the NSA and the MoI of the Slovak Republic is seen as crucial.
Initiation segment at the state level
The aim of the analysis of needs is to comprehensively understand the dynamics of cyberspace, its threats and the vulnerabilities and specific needs of the state and affected entities. A detailed assessment of the current state of cybersecurity and resilience and current compliance with the provisions of the implemented legislation is needed. In NIS2 terms, the sectors concerned are – energy, transport, banking, financial market infrastructure, healthcare, drinking water, waste water, digital infrastructure, ICT service management, public administration, space, postal and courier services, waste management, production and distribution of chemicals, production, processing and distribution of food, manufacturing (selected sectors), providers of digital services and research. It is also necessary to include other sectors according to Act No. 45/2011 Coll. on Critical Infrastructure13 and Act No. 69/2018 Coll. on Cyber Security11 – industry and agriculture.
Designation of roles and competencies is based on the Act on the Organisation of Government Activities and the Organisation of the Central State Administration No. 575/2001 Coll14. , which states that the tasks related to the expert, organisational and technical provision of government activities are performed by the Office of the Government of the Slovak Republic. The Government may appoint and dismiss its plenipotentiaries to perform specific tasks. The Government may establish its advisory bodies. The advisory bodies of the Government shall perform coordinating, consultative or expert tasks. However, it is unlikely that the agenda of cyber security or hybrid threats would be entrusted to a Deputy Prime Minister, nor that the government would appoint a plenipotentiary for this agenda. Such an approach could also lead to competency conflicts with the NSA. Therefore, the model proposes coordination between the NSA – Government of the SR – MoI of the SK. The Security Council and its working committees and individual ministries may also be involved to the scope of their competencies. These relations are shown in the model in the upper left corner. The authorities responsible for these actions may be different in other countries, but actions should be taken to avoid jurisdictional conflicts and to clearly define the relationships.
In designation of responsibilities and communication flows, the first step is to analyse the existing institutional framework and assess whether the new normative act can be effectively implemented within it. In the conditions of the Slovak Republic, according to the Law 69/2018 on Cyber Security11, the competence in the field of cyber security is mainly performed by the NSA, ministries and other state administration bodies, which are referred to as “Central Authorities” in the model. State administration in the field of critical infrastructure is performed by the Government of the Slovak Republic, the Ministry of Interior of the Slovak Republic, the Ministry of Economy of the Slovak Republic, the Ministry of Finance of the Slovak Republic, the Ministry of Investment, Regional Development and Informatization of the Slovak Republic, the Ministry of Transport and Construction of the Slovak Republic, the Ministry of Environment of the Slovak Republic, the Ministry of Health of the Slovak Republic and the Ministry of Agriculture and Rural Development of the Slovak Republic, in accordance with the Act No. 45/2011 Coll. on Critical Infrastructure13. Such an institutional framework is sufficient for the implementation of new legal frameworks related to cyber security and hybrid threats. In practice, the focus should be on building sufficient human, material and financial capacity. This should include planning, budgeting, dedicated cybersecurity training programmes and exercises, and partnerships with the private sector and research.
The communication flows are based on the mentioned structure and are represented in the model by two-way arrows. The NSA has the main responsibility, and implementation will be closely coordinated with the Government of the Slovak Republic (regarding critical infrastructure as well as overlap with other areas of state management) and with the Ministry of Interior of the Slovak Republic (also regarding critical infrastructure). Subsequently, communication will take place towards individual ministries and other government bodies that are not central authorities.
When analysing the legal environment and legislative changes, it is important to evaluate which national legislation will be used to transpose the new legal standard and whether a change is needed. The transposing law of the NIS2 Directive is Act No. 69/2018 Coll. on Cyber Security and on Amendments to Certain Acts11. According to the available information, the Act will be amended. However, it is not always necessary to amend the law. The new requirements can be implemented by Government Regulation or a Decree of the National Security Authority. Ministerial acts may also be adopted by individual ministries.
Entities identification is related to legislative changes that may have been adopted in the previous step. In the model, this applies to the transposition of the NIS2. The Directive itself does not fully define all the criteria for classification as essential or important entity and leaves some space to national governments as to which actors should be included and in which category. The main factors for assessment are the level of criticality of the entity, the sector in which the entity operates, its size and the services it provides. The distinction between essential and important entities is based on the effort to find balance between risk-based requirements and obligations on the one side and the administrative burden of compliance supervision on the other. The list provided by the NIS2 is indicative and includes only the most important entities. In case of the Slovak Republic, it should be recommended to include among the essential entities all operators of essential services and, according to Act No. 45/2011 Coll. on Critical Infrastructure13, the missing entities for the industrial and agricultural sectors. While digital service providers are typically categorized as important entities, the large number of such actors may warrant their inclusion as essential entities for practical reasons. The NIS2 Directive also permits Member States to designate local public administrations and educational institutions, especially those engaged in crucial research, as essential or important entities. In this regard, it is recommended that public administration bodies up to the district level be classified as important entities, while municipal authorities could be encouraged to comply voluntarily with reporting obligations. As for educational institutions, mandatory inclusion under NIS2 could impose an excessive administrative burden. Therefore, voluntary cooperation and reporting are preferable and should be promoted as good practice.
Preparation segment at the entity level
Following the successful execution of the processes and activities in the initiation segment at the state level, the preparation segment at the entity level follows. From a crisis management perspective, this segment includes two key phases, prevention and planning. The responsibility for the security of networks and information systems lies largely on the essential and important entities. A risk management culture should be promoted and developed, including identification and analysis of risk, risk assessment and the implementation of cyber risk management measures that are proportionate to the risks that exist. Therefore, the governing bodies of essential and important entities should internally approve the cybersecurity risk management measures and supervise their implementation. For this reason, it is necessary to designate a responsible person. In the context of NIS2 Directive implementation, this role is fulfilled by the cybersecurity manager. The cybersecurity manager is tasked with leading all efforts to protect the entity from cyber threats and ensuring compliance with the directive’s provisions. Their role is central in the preparation segment, coordinating the majority of processes across both prevention and planning phases—from initial environmental analysis to the finalization of the entity’s cybersecurity plan. The NIS2 also assigns fundamental importance to the function of the cybersecurity manager. According to its provisions, if an essential entity fails to comply with the regulations and measures imposed by the relevant public authorities, they may even prohibit any individual responsible for management tasks, such as an executive director or legal representative, from performing management functions.
The prevention phase takes into account that the need to achieve the required level of preparedness to increase the resilience of essential entity is closely linked to the risk management process in the model of implementation of cyber resilience. The phase is based on current standards of practice as well as scientific knowledge.
The analysis of the environment is employed to set the context for the risk assessment process. This analysis must be conducted with respect to the internal as well as the external environment of the essential entity under assessment. Due to the high variability of threats that may threaten the affected entities, it is important to share information on cyber threats between the entities as well as with the external environment. Sharing information between each other can increase the level of preparedness of entities in the prevention phase and prevent threats from evolving into cyber security incidents. This information sharing is represented in the model by the dashed line.
Risk assessment is an essential prerequisite for successful crisis response and restoration. In the model, the risk assessment, based on the NSA methodology, is divided into identification and analysis of risk and subsequent risk assessment. The process of identification and analysis of risk can be characterised in terms of the basic risk management model presented in the technical standard ISO 31000:2018 Risk Management15. In the model, these are separate processes of the risk assessment phase. In the field of cybersecurity, vulnerabilities are often discussed in the context of risk analysis. Vulnerabilities are weaknesses or gaps in a system that can be abused to compromise security or to increase risk. There are many vulnerabilities within information systems. It can be insufficient security, whether of networks or hardware, software bugs, un-updated software or outdated hardware, weak passwords and authentication mechanisms, vulnerabilities in protocols and standards, but also relatively trivial vulnerabilities such as social engineering or misconfiguration.
A qualitative risk analysis, as described by the Cybersecurity Risk Analysis Methodology of the NSA16, is used for risk assessment. It consists of a phase for identifying risk scenarios and a phase for evaluating the resulting risk for identified threats, harmful events, or scenarios. Risk scenarios represent specific situations of risk realisation, which may combine various threats and vulnerabilities, resulting in different impacts. The resulting risk within a scenario is determined by the intersection of the respective probability value of the scenario’s occurrence and the value of the impact level it will have. The levels of existing measures, which may influence the probability or impact values, are also considered. The probability is classified into four levels: very low, low, medium, and high. Impact estimation has five levels: trivial, minimal, moderate, severe, and catastrophic. The resulting risk is determined as the ratio of probability to the severity of the impact. Four levels of resulting risk are distinguished: extremely severe (A), severe (B), low (C), and insignificant (D).
Assessed risks are divided into two groups: acceptable risks and unacceptable risks. Acceptable risks can be tolerated, while the focus is on unacceptable risks, which by their nature pose a threat to the affected entities. Their realisation could have severe consequences, and therefore they need to be mitigated. Risk treatment is in accordance with the ISO 31000:2018 Risk Management standard15. In the NSA methodology, treatment is defined as the process of risk modification (typically the implementation of measures to mitigate the risk). Security measures are implemented by the entities themselves, and neither the NSA nor CSIRT units intervene in the process.
If the risk treatment is sufficient, the risk is accepted. However, if the risk treatment is not sufficient, the model outlines two possible courses. The first option, represented by a solid line in the model, returns the process to the beginning of the risk treatment phase. The process is repeated in an effort to sufficiently treat the risk. If these attempts are unsuccessful and the risk remains above the acceptable threshold despite the implementation of preventive measures, the inadequately treated risk must be considered during the planning phase, as indicated in the model by a dashed line.
The acceptance of risk represents the final part of the prevention phase in the model. Risk acceptance is based on its assessment. Accepted risks generally do not pose a significant threat to the entities. However, such risks need to be monitored and regularly re-evaluated within the risk assessment phase. As long as the risk does not become completely insignificant, it requires regular re-evaluation.
In terms of the crisis management cycle and its phases, the next step in achieving the desired level of cyber resilience is the planning phase. The measures adopted during the prevention phase take in this step real shapes and levels, ensuring an adequate response capability of entities in the event of a crisis. The goal of this phase is to reach a level of preparedness capable of responding to various crisis situations. The measures implemented also aim to strengthen the technical and administrative performance of essential and important entities.
In the area of increasing cyber resilience, it is necessary for the entity to hire enough qualified and trained personnel, identify the necessary technical infrastructure, and build partnerships. This order of steps applies if the entity can allocate sufficient budget for these activities. If the entity is unable to secure the required state, it is advisable to implement the entity’s cyber defence through external contractor by purchasing a technical solution from a specialised company. The entity can simultaneously work on gradually recruiting or retraining suitable staff so after some time, part of the activities can be carried out by an internal team. To do this, the entity must identify suitable technical equipment, including software, to protect its information systems.
Planning of procedures and activities is crucial for any organisation to withstand cyberattacks, minimise their impacts, and reduce recovery time and costs. We assume that the entity addresses cyber resilience internally and does not use the services of an external company. The first task is to appoint a responsible individual who will lead the team responsible for planning, in our case, this will be the cybersecurity manager. Their responsibility is to ensure sufficient financial, human, and material resources, as described above.
The basic prerequisite of effective cybersecurity planning is continuous monitoring, which enables the early detection and assessment of potential threats. Modern cybersecurity systems often rely on automated monitoring tools that track selected parameters and provide processed reports to operational staff, rather than overwhelming them with raw data. Another component is the planning of responses if monitoring indicates unusual behaviour of information systems or a direct cyberattack. The response typically consists of three phases: containment of the cybersecurity incident, reaction, and restoration of systems. Subsequently, lessons learned and examples of best practices are further analysed. These processes are described in more details in the response segment.
The output of the preparation segment, considering the results of the risk assessment, should be a security plan developed by the entities. The plan must include a description of individual risks, their possible manifestations and consequences, as well as the specific security measures, and the determination of the resources, procedures, and activities that can be used in the reaction phase to crisis events. The security plan, especially for essential entities considering the NIS2 Directive and elements of critical infrastructure according to the applicable legislation of the Slovak Republic, includes all findings and results from the previous processes of the preparation segment. These entities adopt security plan to increase their cyber resilience, protect against cyber threats, withstand potential attacks and in the event of a successful attack, minimise losses, the duration of system outages, and effectively restore their operations. This comprehensive approach goes beyond cybersecurity, increasing the overall cyber resilience of the entity, the processes for addressing cyber security incidents and recovering from them, and highlighting the need for resilience in all aspects of the organisational structure.
The outcome of this segment is the entity’s preparedness to withstand cyber threats, represented as a distinct point within the model. Despite the declared preparedness, it is possible to cyclically return to the prevention phase in the preparation segment, as illustrated by a solid line in the model. This underlines that there is no need to wait for a cyberattack before the prevention and planning phases can be reinitiated. In practice, due to limited personnel and financial resources, this typically occurs at selected time intervals or after a serious cybersecurity incident.
The need to deal with a cyberattack is usually preceded by identification of an attempted attack and efforts to avert it. If the cyberattack is unsuccessful, it is classified a near miss or an unrealised threat. Despite the attack not being successful, the model suggests conducting a forensic analysis, which involves collecting and analysing digital evidence to clarify how the cybersecurity incident occurred, who the attackers are, what tools they used, and what objectives they wanted to achieve. Also, in line with the model’s proposal, a dynamic analysis is also conducted, aimed at monitoring selected parameters in real time and confirming that network behaviour does not differ from comparable periods, thereby confirming the successful averting of the attack. The lessons learned and best practices from the unsuccessful attack are communicated back to the preparation segment, specifically to the analysis of the environment to prevention phase. This is one of the ways in which a new cycle of crisis management is finished and subsequently initiated. If the cyberattack is successful, the process moves into full implementation of the reaction phase.
Response segment at the entity level
In the reaction phase of the model, the initial effort is to identify the attack, its method, and the affected systems as quickly as possible. Once the attack is contained, the focus shifts to minimising its harmful impact and managing the attack successfully. If the attack cannot be managed, attention returns back to re-identify and reassess the fundamental parameters of the attack and the affected systems until a successful management of the attack is achieved. If the entity is unable to manage the successful attack, the relevant CSIRT unit is contacted. Depending on the scale and severity of the attack, other central authorities may also be notified and consulted. Within the model, these relationships are indicated by a dotted line.
During the implementation of the reaction phase, dynamic analysis intensifies within the model, and forensic analysis is also initiated. These two processes are largely interconnected and happen simultaneously. Dynamic analysis aims to monitor selected parameters in real time to detect deviations from normal behavior during comparable periods. Based on these deviations, it is possible to deduce the attack vector and scope of affected systems. Efforts then proceed to contain the attack and disconnect the affected systems. Dynamic analysis continues intensively to verify that containment has been successful. Concurrently, forensic analysis collects and examines digital evidence, which is crucial for various reasons. It helps to uncover how the attack occurred, who conducted it, what tools were used, and why.
In accordance with the NIS2 Directive, the affected entity must notify the CSIRT team or relevant authority within 24 h of detecting a significant incident. The warning can also include information on whether the significant incident was likely caused by illegal actions or if it may have a cross-border impact. At the same time, the entity must submit an incident announcement within 72 h of detection, updating the information provided in the initial warning if necessary and providing a preliminary assessment of the significant incident, its severity and impact. Upon request by the CSIRT team or relevant authority, the entity must provide an interim report with updates, followed by a final report within one month of submitting the incident announcement. This report must include information on the incident, including its severity and impact, the type of threat or the reasons that likely led to the incident, the measures taken, as well as indicating any potential cross-border impact. If the cyber incident is still ongoing at the time, an additional final report must be submitted within a month from the date the incident was solved. These relationships are represented by a dashed line in the model.
In the context of Slovakia, entities report cybersecurity incidents using the unified cybersecurity information system, managed by the National Security Authority (NSA). This system also allows the submission of voluntary incident reports.
As soon as the attack is contained, it is necessary to identify the source of the attack, minimize its harmful effects and eliminate it. Based on dynamic and forensic analysis, various technical solutions are used, from removing the code, to minimizing vulnerabilities, to physically disconnecting certain networks or hardware. It is necessary to make sure that the attacker has lost control and can no longer continue in its harmful actions. The response options are broad and depend on the specific situation. Speed and consistency are crucial. Advanced attacks use code that can modify and replicate itself to pass the detection. Therefore, caution and consistent execution of updated measures are critical to success.
Identifying an attack is not just about eliminating the threat, but also about understanding how the cybersecurity incident occurred. This will prevent it from happening again. There is a need to continue with improved dynamic analysis and scanning of networks for viruses, malware or suspicious codes. Additional security measures such as reinstalling systems, changing passwords, controlling access rights are being implemented. This is where the active role of the CSIRT unit ends and its involvement continues only in the sense of consultation and recommendations.
The restoration phase is the last part of the proposed model, which aims at restoring the full functionality of the systems. This must be done in a secure manner to minimise the duration of the outage and to secure full functionality and security, and to make sure that the information in the system has not been changed.
The basis of this process is to assess the extent of the damage to estimate the duration of the outage and set priorities for restoration. The affected systems, data and equipment must be identified, including an estimate of what damage has been done. The functionality of the systems and the impact on the operations of the affected entity must also be assessed. The results of forensic and dynamic analysis are used, as understanding the nature and vector of the attack helps to understand the reasons and objectives of the attack, which further helps to identify systems that appear unaffected but can be compromised. Dynamic analysis will uncover systems and hardware that are not working properly.
From the perspective of the affected entity’s operations, the priority seems to be to restore all operations as soon as possible. However, the priority must be integrity, i.e. the assurance that the integrity, completeness or correctness of the information has not been compromised. Having said that, available resources should be used efficiently so the recovery of critical parts of the system could be addressed and the duration of the outage could be minimised. It is also important to recognise the dependence of systems and to recover in groups those systems forming an organic unit together. At this moment, it is also important to inform managers of the concerned entities of the steps that are being implemented, explain their sequence and propose a course of further action.
The restoration of continuity is preceded by testing and control. In particular, the functionality of the systems is tested, whether they are working correctly and achieving the required performance parameters, the security of the systems, whether all vulnerabilities have been eliminated, and the integrity is also tested, whether all recovered data are error-free, complete and correct. Various automated, diagnostic tools are used, manual testing may also be required. Certain proportion of users are included to confirm the functionality and integrity of their data as required. Service restoration may be gradual. In most cases, all systems are rebooted once more and restarted according to their importance before final start-up. It should be communicated to users which systems are already operational, where outages may occur, or where functionality can be limited. Also, monitoring is carried out to continuously confirm that the restoration of service is proceeding correctly, that no harmful code has reinfected the systems during the restoration, or that an attacker has not regained access to the systems.
The vertical panel of the model to the left of the main section, shows the coordination, cooperation and control by central authorities. The panel also indicates that collaborating entities can share their lessons learned and best practices with these authorities. The model also contains a solid line indicating that, once one crisis management cycle has been completed, the lessons learned and good practices are used again in the next cycle, which starts in the preparation segment, in the prevention phase. The dashed line, which links the conclusion of the model to the external environment, comes from the same place. This is where consultation with other entities, possibly the security community, the private sector and academia, takes place.
Verification of the model at the entity level
The purpose of this exercise was to verify the part of the proposed module dedicated to entities, more specifically the preparation segment and the response segment. The prerequisite was the implementation of the initiation segment at the state level. The model was verified through a structured table-top theoretical exercise. The entity-level part of the model was assessed in seven functional parts. The assessment was carried out in seven parts according to the proposed model.
1.
Designation of a responsible person—it was examined whether the company has a designated person responsible for the area of cybersecurity. The responsible person is the Cybersecurity Manager, who is appointed by the company’s management and is indirectly accountable for carrying out activities in the field of information and cybersecurity. It was concluded that this part is sufficiently comprehensive and feasible in practice. No modifications to the model were proposed, and its implementation in real practice was recommended.
2.
Analysis of the environment—it was noted that, given the standardized environment in which the company’s core activities take place, an analysis of the environment is not conducted on a regular basis. This activity partially overlaps with similar tasks within the solution segment. However, it was concluded that conducting cyclical analysis of the environment and the related context assessment would be beneficial for both the prevention and planning phases. It was concluded that this part is sufficiently comprehensive and feasible in practice. No modifications to the model were proposed, and its implementation in real practice was recommended.
3.
Risk assessment—risk assessment within the organization is carried out on an ongoing basis, based on the premise that it serves as the foundation for both prevention and an effective response to a crisis event. It was also noted that the internal directive is in full compliance with all requirements for IT risk management as set out by the relevant standards. Risks are continuously identified and analyzed. It was concluded that this part is sufficiently comprehensive and feasible in practice. No modifications to the model were proposed, and its implementation in real practice was recommended.
4.
Risk treatment and acceptance—the approach to risk treatment and its subsequent acceptance was discussed. Risks may be identified either by an employee or automatically through automated monitoring. They are also detected during audits and are commonly identified in the course of project work. The company maintains its own risk catalog, which plays a key role in the risk identification process. Identified risks are compared against the catalog to determine whether they have already been recorded. Risk assessment is carried out in multiple phases, as outlined in the proposed model. Once a risk is identified, a risk owner is assigned. Only after that is the risk formally assessed. The company uses a semi-quantitative method, evaluating information risks based on likelihood and impact, each defined using a five-level scale.As part of the risk treatment process, a responsible person is again designated to oversee the risk and to prepare a report on the treatment measures taken. This is usually the risk owner, however, it is a strict requirement that the individual be an internal employee with the appropriate level of authority. Risk treatment and acceptance are not based solely on the risk matrix, which determines the final risk level as a combination of likelihood and impact, but also take into account the additional costs required for risk treatment. It was concluded that this part is sufficiently comprehensive and feasible in practice. No modifications to the model were proposed, and its implementation in real practice was recommended.
5.
Planning phase—the planning phase partially overlaps with the prevention phase in the sense that, during the identification of resources and finances, priority is given to unacceptable risks that could not be adequately treated in the previous stage. The plan of procedures and activities is closely linked to the development of the security plan itself. The security plan may be, and in the company’s, case is, replaced by security documentation. Once the security plan or security documentation is finalized, security monitoring is carried out based on the parameters defined therein. It was concluded that this part is sufficiently comprehensive and feasible in practice. It was recommended to consider merging the section “Plan of procedures and activities” with the section “Security plan”. Implementation in real practice was recommended.
6.
Reaction phase—in the case of an event that has not previously been observed, the event report would, as suggested by the proposed model, be used within the preparation segment. Practice shows two key observations. First, the majority of cyberattacks tend to recur or share similar characteristics. Second, a new type of cyberattack is not always assessed as a risk during the prevention phase, instead the process may move directly to the planning phase, with the aim of deploying available resources and finances to strengthen the company’s resilience against the new type of attack. If sufficient financial resources are available, new tools may also be procured to enhance resilience. In the event of a successful cyberattack, standard procedures would be carried out as illustrated in the model. The method and scope of the attack are identified, followed by efforts to contain it. Both forensic and dynamic analyses are conducted. This is followed by actions to minimise the harmful impact of the attack and to ensure its successful mitigation. If the attack cannot be contained or exceeds internally defined thresholds, coordination with the CSIRT unit is initiated. It was concluded that this part is sufficiently comprehensive and feasible in practice. No modifications to the model were proposed, and its implementation in real practice was recommended.
7.
Restoration phase—Verification showed that the method of recovery largely depends on which systems were affected. In all cases, it is a complex process that must be divided into multiple phases. The three components proposed by the model were assessed as appropriately chosen. A properly executed recovery phase is important not only for enabling the company to recover from the immediate impact of the attack, but also for strengthening its defenses against future threats. Before recovery begins, a basic recovery plan was established during the exercise, assessing the importance of individual systems and considering the complexity of recovery in terms of time, resources, and finances. Factors influencing the method and order of system restoration also included the potential operational, financial, and reputational damage that could result from prolonged downtime of any system. Based on the plan, the actual system recovery process was carried out. Throughout the recovery, progress was continuously evaluated and, if necessary, the approach was adjusted.The final step of the recovery phase, and the concluding outcome of the entire response segment, is the restoration of service continuity. As part of restoring service functionality, the last step involves a “go-live check,” which tests the service from the perspective of various user roles. At minimum, this includes checking the main functional features and the completeness of the data. This testing also helps identify any remaining issues that need to be addressed before full operations can resume. It was concluded that this part is sufficiently comprehensive and feasible in practice. It was recommended to rename the section “Restoration of service continuity” to “Full functionality of systems and services”. Implementation in real practice was recommended.
In each part, applicability was considered in four areas: the complexity of the model in terms of possible missing elements, the feasibility of the model in practice, suggestions for modification of the model after its application, recommendation for application in real practice.
The results of the verification are included in the discussion, where they are given additional attention. All recommendations from the verification have been implemented into the model to make it fully applicable.
Defining the term cyber resilience
The academic community is increasingly talking about the term cyber resilience. It could become an umbrella term having a wider understanding of the actions, that are necessary to improve resilience of various subjects against cyber-threats. Therefore, authors decided, as a side-line to explore this term and came up with their own definition of the term. Creating the definition was a theoretical challenge with a complex, related process, in which it was necessary to analyse a significant amount of Slovak and foreign sources. The definition of cyber resilience was different for each author. Some authors based their definition on four, some on five basic elements, others offered definitions for different horizontal levels from the enterprise to multinational groups, or they perceived the whole concept of cyber resilience differently. Their view of the concept of cyber resilience provided the knowledge base for the definition. The need for a definition of cyber resilience comes from the absence of this definition in national structures despite the use of the term. The purpose of the definition is also to appropriately complement the model where the focus is on prevention, planning, response, recovery and adaptation. For the wide application of the definition, it must be accepted by the entire Slovak security community. Furthermore, such a definition must consider national specificities, national legislation in this area and new European legislation. The proposed definition based on an analysis of other definitions and many additional resources is: Cyber resilience is the ability or internal characteristic of an entity to maintain continuity of delivery of expected services at the required level, while maintaining the confidentiality, availability, authenticity and integrity of the information provided in a breached cyber environment. It is the ability of an entity to resist attempts to fulfil threats against its information and communication systems, to minimise the impact of those threats, and to recover functionality and to adapt.
Defining the relationship between cyber resilience and cyber security was also problematic. There is currently no clear answer, as the issue is currently being addressed by several academic institutions with different perspectives, approaches and their own arguments. However, it can be stated that cyber resilience and cyber security are closely interlinked with common activities and areas they address. The proposed definition reflects national specificities, domestic legislation in this area, and the new European legal framework, which may contribute to its acceptance. Even if ultimately not adopted, its evaluation can contribute to the professional discussion on the concept of cyber resilience.