Project Leap 2 is not a theoretical experiment or an academic exercise. It is a test conducted on real payment systems, with liquidity transfers and infrastructures that cannot afford errors or slowdowns. The Bank of Italy has published the results of the second phase of the project coordinated by the BIS Innovation Hub, bringing post-quantum cryptography within an operational perimeter where stability, continuity and reliability count. The point was not to prove that the algorithms work in the abstract. That was already known. The real goal was to understand whether they hold up when embedded in complex, layered, interconnected systems. This is where Project Leap 2 stops being a ‘research’ project and starts speaking directly to the financial sector.
Why Project Leap 2 was born out of an existing risk
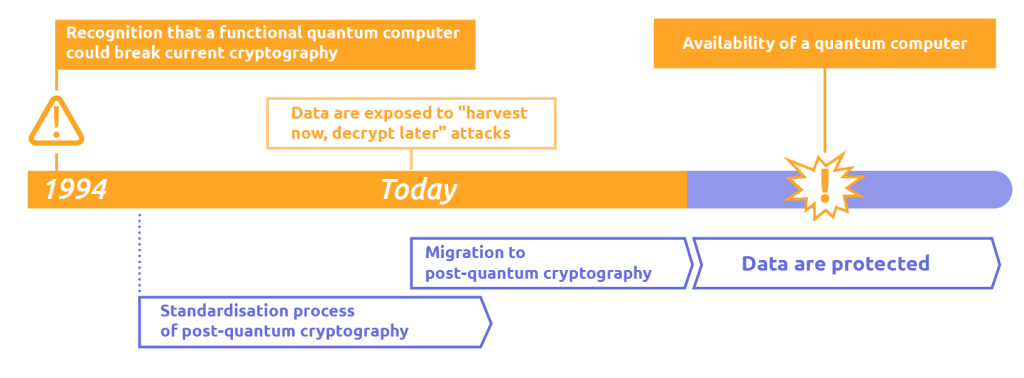
The security of payment systems is still based on public key cryptographic algorithms used for digital signatures and message protection. These schemes are robust against traditional computers, but are not designed to withstand sufficiently powerful quantum computers. The risk is not only in the distant future. Encrypted data today can be intercepted and stored with the aim of decrypting it later, when technology allows. In the financial sector, this scenario weighs more heavily than elsewhere. Payment data retain value over time and core infrastructures do not update quickly. Waiting would mean having to intervene in an emergency. Project Leap 2 was created precisely to avoid this scenario.
From laboratory to operation: the leap of Project Leap 2
After an initial phase dedicated to the secure exchange of messages between central bank systems, Project Leap 2 shifted the focus to operational payment systems. Here, every change has a direct impact on reliability, interoperability and processing times. It is not a context in which one can experiment without consequences. The second phase of the project involved, in addition to the Bank of Italy, the Banque de France, the Deutsche Bundesbank, SWIFT and technology providers such as Nexi-Colt. The objective was clear: to test whether post-quantum cryptography could be integrated without compromising the day-to-day functioning of the infrastructure.
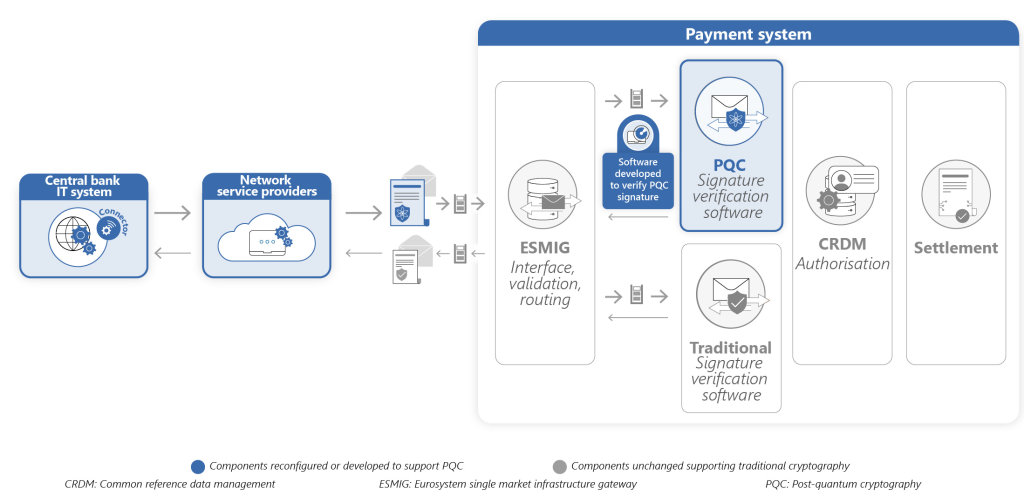
What was actually tested in Project Leap 2
In the course of the experiment, traditional digital signatures were replaced with signatures based on post-quantum cryptographic algorithms during the execution of cash transfers. To make this transition possible, it was necessary to work on various system components, update cryptographic libraries and verify compatibility between heterogeneous infrastructures. All planned scenarios were successfully completed. Payments were processed correctly and the system proved to be able to operate even with quantum-resistant cryptographic schemes. Project Leap 2 thus confirms the technical feasibility of the migration, but without concealing the critical issues that emerged.
Performance and overhead: the real crux of the test
The most sensitive point concerns the impact on performance. Post-quantum encryption algorithms require more computational resources and introduce increased processing times compared to traditional solutions. In payment systems, where speed is not a detail but a structural condition, this aspect assumes strategic importance. Project Leap 2 clearly shows that the transition to quantum-safe cannot be approached as a simple software upgrade. It will require planning, investment and an overhaul of IT architectures, especially for high-volume systems.
The regulatory significance of Project Leap 2
The publication of the results by the BoI should also be read from a regulatory perspective. Central banks are indicating that quantum risk is considered a component of systemic resilience and not a futuristic issue. It is plausible that, in the medium term, post-quantum cryptography will enter into supervisory expectations and technology audits. Although Project Leap 2 directly concerns central banks, the message is aimed at the entire financial ecosystem. Payment systems are interconnected, and securing the core will inevitably entail securing the peripheral layers.
A long transition that must be started now
Project Leap 2 does not say that the problem is solved. It says that ignoring it is no longer an option. The time window to prepare exists now, not when quantum computers will be fully operational. Starting the transition early allows the change to be managed gradually, reducing the risk of emergency interventions. The signal is clear. The security of payment systems in the next decade will also depend on the ability to deal with the quantum threat in time.
