Executive Summary
Identity is now the #1 attack surface. Agent Grant in Qualys ETM Identity uses agentic AI to measure and reduce identity risk across AD, Entra, Okta & other cloud IdPs/IDaaS. It operationalizes identity risk by turning messy Active Directory & identity-risk signals into validated, prioritized, and closed-loop actions with proof of risk removed.
Identity has quietly become the enterprise’s soft underbelly – the most exploited and least quantified attack surface, leading to widespread identity exposure.
Over 74% of breaches now involve a compromised identity — human, machine, or service. Yet, most IAM and compliance programs still report on control status, including password rotation rates, MFA coverage, and dormant accounts. These are motion metrics, not outcome metrics.
The real question isn’t how many controls are in place, but how much exploitability remains. Effective IAM risk management must address the gap between governance and measurement — weak AD hygiene, misconfigured Conditional Access, over-entitled service accounts, and hybrid directory drift.
The missing element is evidence: a way to show that a change actually reduced exploitable risk. That’s the problem Agent Grant was built to solve.
From Reactive Controls to Agentic AI
Cybersecurity tools often stop at visibility, collecting data and displaying dashboards, without enabling action.
Identity security is trapped here: we know which accounts are stale or over-privileged, but fixing them still requires tickets, approvals, and manual work that takes weeks, while attackers exploit gaps in hours. The problem has worsened across hybrid identity systems, such as AD, Entra ID, Okta, and SaaS apps, where misconfigurations can drift faster than humans can correct them.
Qualys addresses this by embedding an Agentic AI fabric into its Enterprise TruRisk Management (ETM) platform, enabling a transition from human-paced triage to autonomous risk optimization. Instead of hard-coded workflows, agentic systems reason through planning, decision, action, and feedback loops — executing only what measurably reduces risk within policy guardrails.
For identity, that means transitioning from control compliance to continuous optimization: How fast did we shrink exploitable exposure, and what is the evidence? That’s the intelligence Agent Grant, the first agentic AI for identity, brings to the most abused entry point in the enterprise: your Login screen.
Introducing Agent Grant in Qualys ETM Identity
Every Qualys agentic AI has a domain. Agent Nova interprets open-ended security intent across asset and vulnerability data. Agent Nyra drives threat-informed prioritization. Agent Vikram focuses on adaptive cloud posture.
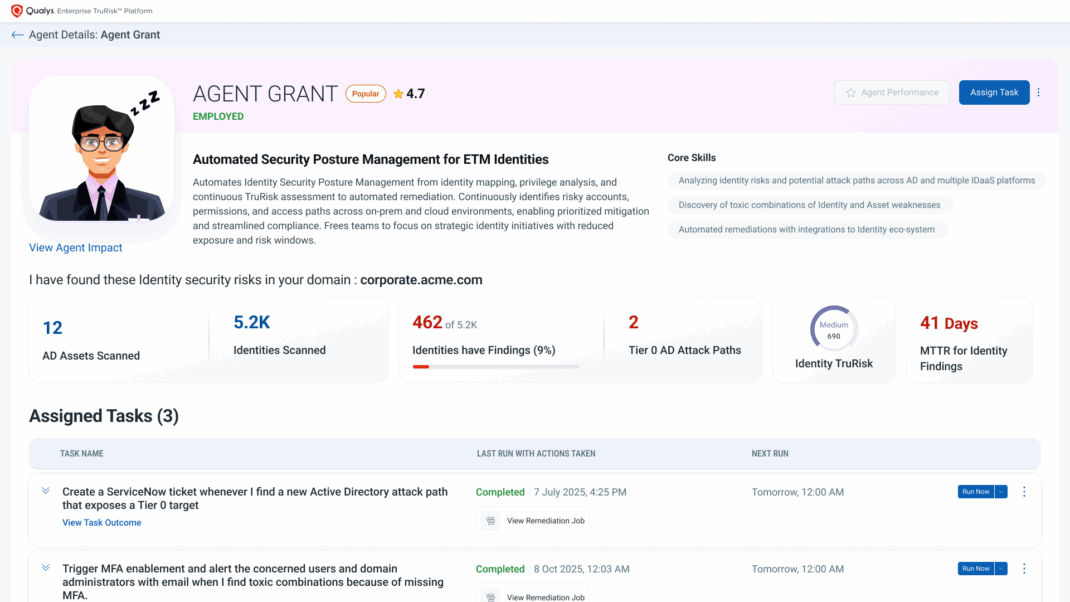
Agent Grant is Qualys ETM Identity’s domain-specific intelligence — a cyber-risk analyst that continuously collects telemetry from across AD, Entra ID, Okta, and other IDaaS/IdPs, correlates users, service accounts, machine identities, entitlements, with asset and vulnerability context to compute Identity TruRisk™, a quantitative score that expresses how identity weaknesses expand or shrink your overall attack surface.
Agent Grant’s mission is simple: Turn identity sprawl into measurable, reduced risk.
But correlation is only step one. Agent Grant then applies policy-aware reasoning to determine the next course of action. It weighs exploitability, privilege scope, business impact, and compliance requirements before recommending or executing actions such as:
Disabling or quarantining high-risk accounts
Enforcing or repairing MFA and password policies
Reducing toxic group memberships and stale entitlements
Isolating devices tied to compromised identities using Qualys TruRisk Eliminate
Initiating patch or mitigation workflows using Qualys TruRisk™ Eliminate
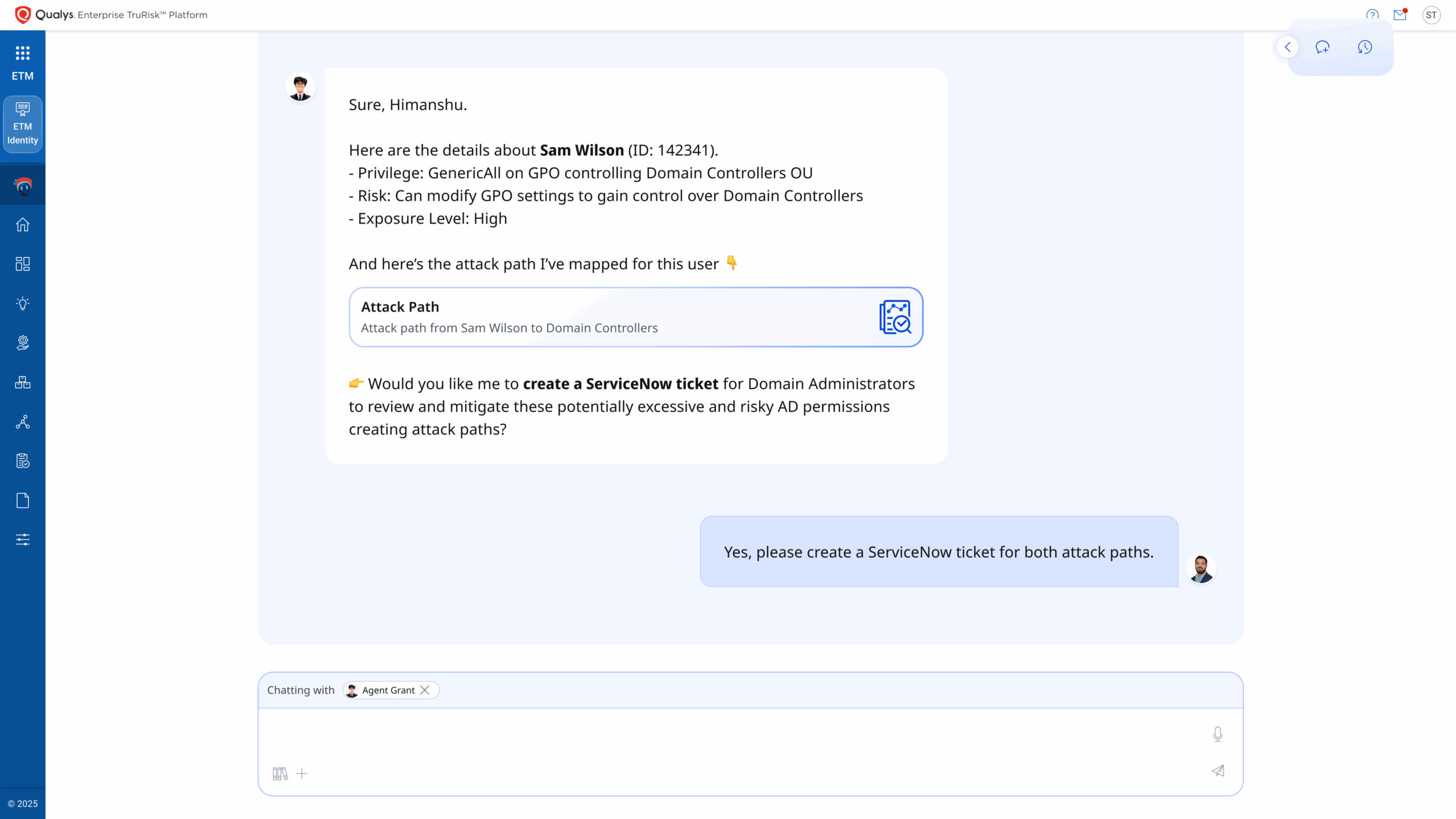
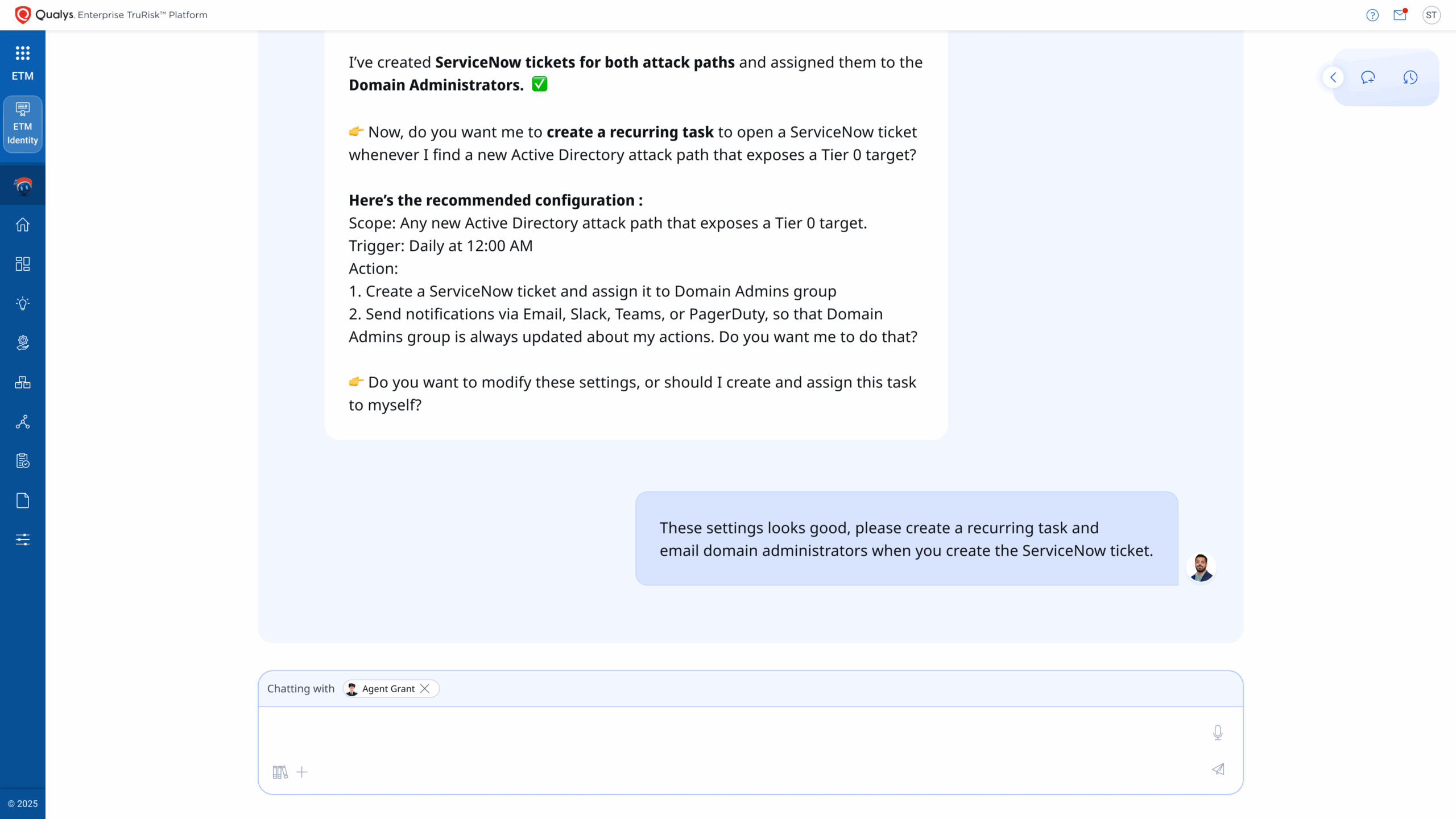
Automating remediation workflows across ITSM systems like ServiceNow/JIRA
Each action is run within ROC guardrails, ensuring that every change is logged, approved, and measurable. Agent Grant then validates closure, verifying that exposures truly disappeared—not just moved to another directory. The updated TruRisk™ score becomes live evidence of risk eliminated.
The Evidence Loop — Prioritize, Validate, Eliminate
Agent Grant operates on a continuous Evidence Loop that replaces guesswork with measurable causality:
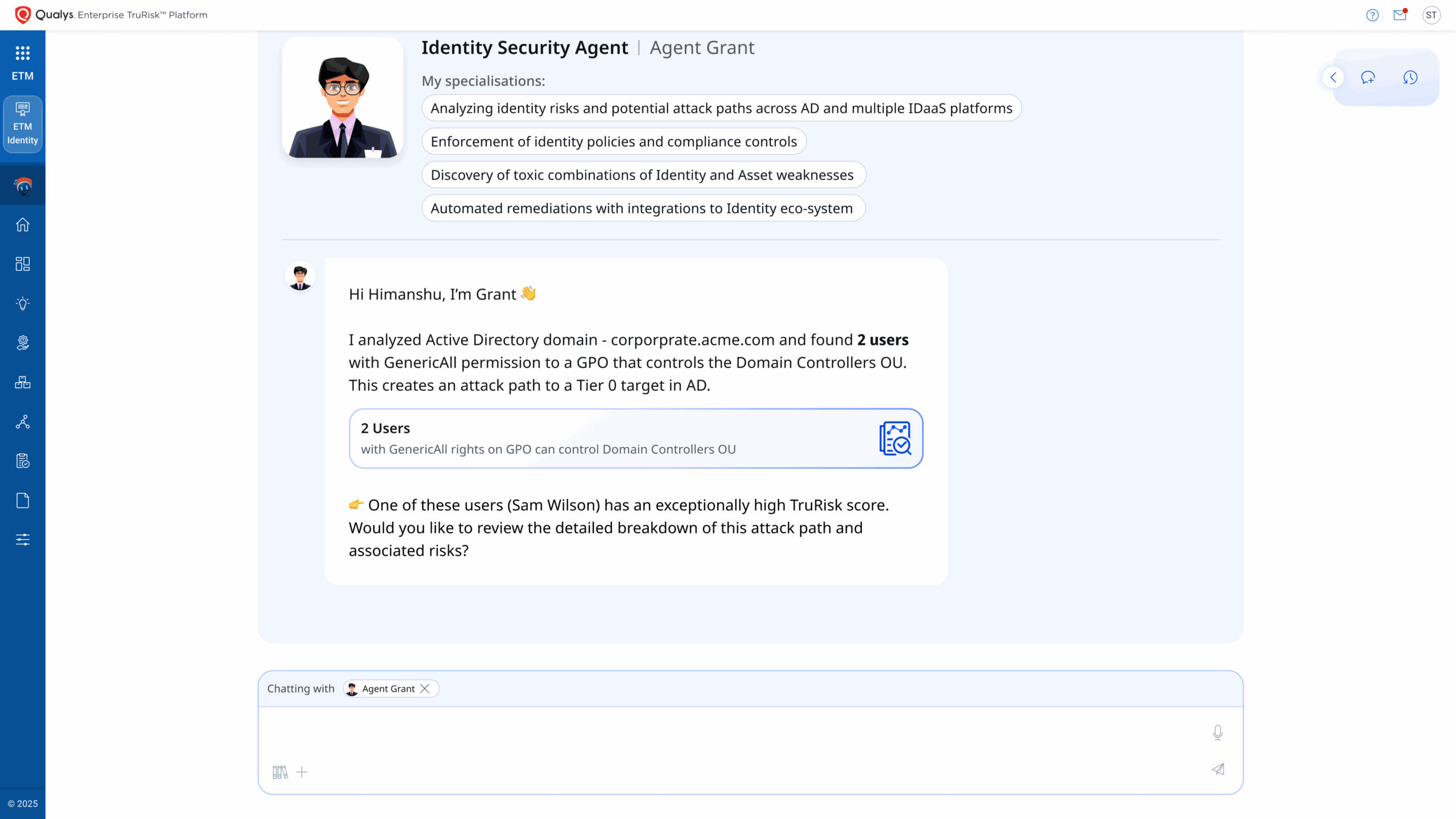
Prioritize with context – Weighs each exposure by industry relevance, business criticality, and exploit likelihood. For example, an expired service-account password in a sandbox domain may rate low, while the same condition on a domain controller running critical workloads might rate exponentially higher.
Validate exploitability: Uses TruConfirm™ to test whether an exposure or a weakness can be abused in practice, such as determining whether a weak password is reachable from an attack path, or whether conditional access can be bypassed, filtering out noise.
Eliminate with action: Orchestrates remediation through policy-aware actions, such as disabling, isolating, enforcing, or patching, whichever delivers the maximum TruRisk reduction per unit of effort. Every action is measured for before-and-after TruRisk™ deltas.
The loop turns every fix into verifiable evidence. Security teams finally understand what changed, why it mattered, and how much risk it mitigated, along with a narrative that finally reads in the language of risk reduction per dollar spent.
How Agent Grant “Thinks”
Most automation in security is procedural: if A, then B. It’s deterministic and effective only when the world stays predictable. Identity doesn’t. Permissions drift, SaaS tenants spawn shadow admins, and “temporary” exceptions age into permanent attack paths. A static playbook can’t reason about that chaos.
Agent Grant doesn’t follow static playbooks. It operates through what Qualys calls agentic loops, closed systems of planning, reasoning, acting, and learning, inspired by the same AI research now powering adaptive cyber operations. This is the core of Agentic AI identity security. These loops allow Agent Grant to make judgment calls that traditional automation can not.
When a CISO says, “Reduce stale service-account blast radius,” Agent Grant decomposes that intent into discovery, correlation, exploit scoring, and remediation steps — all grounded in TruRisk™ context.
CapabilitiesDescriptionsPlanning & Tool UseDecomposes intent into executable queries and actions.Governed AutonomyOperates under ROC approvals and rollback controls.Continuous LearningAdapts to outcomes; successful actions reinforce future decisions.Shared IntelligenceExchanges reasoning patterns with sibling agents — Nova, Nyra, Vikram — forming a collective AI fabric across ETM.
Identity Attack Surface — What Agent Grant Targets First
Every organization has a “known-unknown” zone in its identity layer — accounts, entitlements, and trusts that technically exist but practically escape oversight. This is where attackers thrive, and this is where Agent Grant begins.
Agent Grant prioritizes identity weaknesses with the highest breach correlation:
Weak AD Hygiene: 200+ checks covering password/MFA policy gaps and toxic GPOs.
Excessive Privileges: Cross-domain admin rights and stale entitlements.
Service-Account Risk: Detection of Kerberoastable accounts, plaintext secrets, and unused keys.
Hybrid IdP Drift: Misaligned policies across AD + Entra + Okta + SaaS tenants.
Shadow SaaS Identities: Local accounts and OAuth Grants expand the attack surface.
The outcome isn’t more findings. It is fewer exploitable conditions, verified and visible in the Identity TruRisk™ score.
What’s Next
Cybersecurity has no shortage of dashboards, metrics, or promises. What it lacks is proof — proof that actions taken today measurably reduce tomorrow’s breach probability. Agent Grant, the Agentic AI for Qualys ETM Identity, delivers that proof. It quantifies identity exposure, validates exploitability, and automates remediation inside the guardrails of your Risk Operations Center.
Agent Grant is a new class of policy-aware, self-auditing AI agents inside ETM.
Non-Human and Agentic-AI Identities: Extending identity governance to service accounts, API keys, and emerging AI entities acting autonomously.
Predictive Risk Modeling: Leveraging TruLens analytics to forecast identity failures before they occur.
Collaborative AI in the ROC: Agents like Grant, Nova, Nyra, and Vikram cooperating across identity, asset, and cloud surfaces to orchestrate closed-loop reduction.
Future readiness means proving not only that identities are managed, but that the agents managing them are measurable, trustworthy, and accountable.
Get started with ETM Identity
Start a 30-day trial of ETM Identity and target your riskiest identity cohorts.
Related