In this section, we examined the working methods, applications, and research limits of current schemes. As a result of the advent of the digital age, numerous industries have been presented with an abundance of opportunities and innovations, which have been characterized by an ever-increasing dependence on technology. However, these improvements also carry with them several challenges, particularly in the realm of cybersecurity9. Insider threats, also known as damaging activities that originate from within an organization, have emerged as a significant worry in recent years, despite the fact that outside threats have traditionally been the primary focus of security measures10.
The use of a trustworthy server that saves the data is a common feature of the methods now in use. Access control relies on software checks to ensure that a person can access a piece of data only if authorized. From a security perspective, this arrangement is not very desirable. We then encrypt the data using the public key of the intended set and classify it according to the hierarchy. There are some drawbacks to these techniques. If a user of a set needs to provide access to a third party to access data for that set, the user must either provide the third party with their private decryption key so that it may access all entries or act as an intermediary and decode all relevant entries11.
In contrast to conventional PKI, identity-based public key cryptography (ID-PKC) addresses the issue of key authenticity through various procedures. An entity’s public key in ID-PKC is directly obtained from distinct characteristics of its identity, such as an IP address that belongs to a network host or an email address that is connected to a user. The public key generator (PKG) constructs private keys for entities. Before launching an attack, the adversary in a typical PKI must issue a new certificate and persuade entities to accept the new public keys. These factors suggest that applications with low-security requirements or small, closed groups could be the only ones permitted the user ID-PKC12.
The authors present a brand-new public key cryptography paradigm, referring to it as certificateless public key cryptography (CL-PKC)13. The search for public key schemes without requirements for certificates and without ID-PKC’s built-in key escrow capability provided developers with the idea of CL-PKC. One of the most important issues with public key infrastructures (PKIs) has always been the efficient revocation of public key certificates. In RSA-type cryptosystems, Boneh presented a technique for getting instantaneous revocation of a user’s public key privileges14.
According to the description, the system known as mediated RSA (mRSA) uses threshold RSA, in which both parties share the private key. The encryption and verification processes in the SEM architecture are identical to those in traditional RSA, making it transparent to both the sender and the verifier of a signature. Additionally, adopting SEM design eliminates the requirement to check a public key’s status before using it. Users don’t need to worry about any certificate’s validity before using another user’s key to encrypt a message.
Identity-based cryptosystems are another way to streamline key management. This idea was first presented by Shamir in 1984, with the goal of removing as many public key certificates as feasible by enabling a public key to be uniquely generated from the user’s identifying data like email address, phone number, and social security number15.
Additionally, it makes key management simpler because there’s no need to maintain a huge database with a list of public keys and their owners. COVID-19 had a significant impact on the healthcare industry, which was the global pandemic problem. The COVID-19 outbreak resulted in an exponential increase in demand for IoMT devices, which then impacted the global market. The IoMT dramatically reduces patient costs, easing the financial strain on individuals and governments. According to a report published by Fortune Business Insights on August 26, 2024, the IoMT market was estimated to be worth USD 47.32 billion in 2023. During the projection period, the market is expected to increase from USD 60.03 billion in 2024 to USD 814.28 billion in 2032, with a CAGR of 38.5 %16.
The authors present a sensor cloud architecture that uses virtualized physical sensors and dynamic sensor placement based on patient movement and health to continuously monitor high-risk patients17. The research uses a threat model to address wearable payment security. For near-field communication pairs of devices, ECC encrypts messages, and biometrics authenticates safe payments18.
The authors present an identity-based signature system without key escrow that issues private keys without a secure connection. It employs binding–blinding to avoid key escrow and eliminate the need for a secure connection during private issuance19. To ensure the confidentiality of patient information while it is shared and integrated across healthcare providers, they offer a system based on knowledge graphs20. Fog computing with private blockchain offers a trustworthy method of storing and transferring patient data while simultaneously improving the identification of security risks and bolstering the privacy and security of medical data21.
The MD5 hash technique securely stores user passwords for use in authentication procedures. Integrating an MD5 checksum into the original patient record file presents an additional barrier to security and verification22. To create a cryptographic method that satisfies the essential requirements of contemporary smart healthcare cyber-physical systems, the research uses ECC, hash functions, and digital signatures23.
An authentication strategy for IoMT devices is proposed to enhance the security and performance of existing authentication schemes. Through the development of an offline authentication model that directly checks identities, the suggested authentication system successfully authenticates users and IoMT devices within the local area network24. A scalable and adaptable distributed group key agreement protocol is used to reduce CPU overhead by running elliptic curve Diffie-Hellman using multiplications instead of exponential calculations to secure data transmissions in WSN25.
The prospect of IoMT-related attacks poses the most severe threat to the security and privacy of patient medical records. The suggested approach protects the secrecy of IoMT devices linked to the patient’s body while communicating. The XOR operator, hash function, and concatenation were used to save processing power26. An authenticated key agreement protocol for the IoMT using elliptic curve encryption and zero-knowledge proof methods is used to preserve the privacy of patient’s critical information27.
In order to secure the transfer of medical records, a research uses signcryption with an identity-based authentication system based on elliptic curve cryptography. Based on bilinear pairing, the suggested protocol covers a number of security characteristics, such as data confidentiality and authentication with efficient key management28.
iSecureHealth, a lightweight and reliable key exchange mechanism, addresses security, authentication, and privacy issues. To secure communication between IoMT sensors and the gateway node, it adds a security control node. The system uses ECDH for key exchange and HMAC-SHA256-based JSON Web Token for session key creation29.
Our goal in writing this paper is to add to the increasing quantity of information on insider threat detection by providing theoretical understanding and useful solutions to one of the most important cybersecurity problems of our day. The relation between various existing security models, threat models, and their limitations is discussed in Table 1.
Table 1 Relation between various related security schemes and its limitations.Health monitoring with body sensors
Wireless Sensor Networks are also utilized for in-home patient monitoring. A system for distributed telemonitoring was proposed. It employs the Services Layers over the Physical Devices paradigm. The architecture model is service-oriented. The distribution of resources among several WSNs is the primary goal. This concept can also link several networks with different wireless technologies. The device was placed within the patient’s home and gathered motion data and several feature values, such as activity, mobility, and non-response levels. To distinguish between normal and pathological behaviors, the Support Vector Data Description method was applied. An algorithm for categorizing behavior patterns was employed to group the patterns in this instance. There is no evidence to support the expectation that these methods will work in a home setting30,31.
A Body Sensor Network with several body sensors is developed for the best possible resource allocation. This solution effectively addressed the two main issues facing health monitoring systems: a sustainable power source and quality of service. A survey was conducted on wearable sensor-based health monitoring systems. Evaluation aspects led to the evaluation of several systems32,33.
The Wireless Patient Portable Unit, which is likewise affixed to the patient’s body, received data relating to cardiac monitoring that was continuously recorded in the home module. The Wireless Access Point Unit was then used to transfer it via the Internet to the hospital. If the doctor notices any irregularities in the signals the patient got while in the hospital, they can get in touch with them, offer some guidance, or, in an emergency, send an ambulance to the patient’s home. This technology does not provide security or surveillance of the outer environment.
Health monitoring using smart phones
Wearable sensors served as the foundation for the sensor network. The sensors obtained the patient’s vital signs, which were then sent to the patient’s mobile phone. The data is safely received, stored, and sent to reliable medical specialists by the mobile device. Only the data’s accessibility to outside parties is under the patient’s control. No PC was utilized in this process; instead, all tasks were completed via mobile device. The handheld gadget transfers only the relevant data after data mining techniques were applied to filter out extraneous data sequences. The expert’s equipment and the patient’s mobile phone communicated over Bluetooth or WLAN 802.11. When an emergency occurs, the patient’s device generates an emergency call, which is then routed to the caregiver’s device.
A brand-new Wearable Mobility Monitoring System was unveiled. It recognized a state change and utilized a smartphone to take pictures. A solution for on-demand tracking and placement was suggested. It was designed for vast spaces and was based on devices with Global Positioning enabled. The first communication between the two terminals was done via a smartphone.
First communication takes place during the synchronization phase. In this case, the requested terminal T1 sends the desired terminal T2 a synchronization Short Message Service (SMS). T2 completes the operation if it rejects the message. If not, the terminal’s position is sent in one of the following formats: multimedia (MMS) or text (SMS). The graphic that shows the position map of the terminal was present in the multimedia format, but the text format just contained the coordinate values of the terminal. A straightforward Peer-to-peer (P2P) protocol is used to facilitate communication between two terminals.
Health monitoring with security
For health monitoring, various security and privacy protocols were applied34. The patient’s vital signs were transmitted, stored, and received via a smartphone. A multimedia format was provided between sensors and the central hub encryption scheme, which depicts the location map of the terminal. Peer-to-peer (P2P) protocol is a straightforward means of communication between two terminals.
Cipher text Policy Attribute Based Encryption (CP-ABE) with security enhancement techniques was presented. The two main issues in CPABE were the user revocation and the key escrow problem. In CP-ABE, a set of user attributes is applied to KGC’s master secret keys, allowing KGC to produce the users’ private keys. Because KGC may decrypt user ciphertext to obtain the original data, it was not considered trustworthy. It is called the “key escrow problem.” Users may periodically alter their properties or certain secret keys may be hacked. Regular updates are required for every characteristic to keep the system secure. We refer to this as user revocation. Both of these issues were resolved35.
Threat model
This subsection covered privacy and security breaches involving patient data. The threat model primarily targets the cybersecurity domains of application-level security, communication-level security, and device-level security. We will discuss the following points related to threat model:
-
We analyze a robust adversary model, assuming that, except for the certificate authority, we cannot fully trust any of the entities. Though strange, the hospital and payment gateway are regarded as trustworthy.
-
External adversaries could listen in on the conversation and deduce private information about patients as the records are being transmitted.
-
To fraudulently accuse lawful patients of overspending, attackers may initiate collision assaults.
-
While paying a doctor’s charge or ordering medicine online, an eavesdropper may attack the system by providing false information or by pretending to be another real patient, utilizing their hospital account.
-
Multiple system attacks may compromise employee privacy when client-server communication stores and forwards private information to several external parties. Via network vulnerabilities or the acquisition of the access point identifier, the attacker, for instance, can seize the patients and examine the network traffic.
-
Problems with data communication arise when sensitive data is sent and processed between different detachments participating in the transmission security and privacy problems arise.
-
Problems with digital devices and Internet of Things devices, as well as the outcomes for patients using these devices.
-
The stakeholders that are considered in the framework are the entities that are a part of this entire procedure (e.g., hospital servers, employees, and patients).
-
Digital electronic devices that are incorporated with advanced cryptography tools preserve patient data.
The prevalence of attacks came from the communication and application levels, which we addressed and stopped. The adversary may launch significant assaults and seriously harm financial institutions and other protocol participants if they discover any gaps or vulnerabilities in these areas. We are using the lightweight cryptography techniques provided by ECDSA to create and validate signatures. Similar to this, we have employed the elliptic curve integrated encryption scheme (ECIES) as an asymmetric method of encryption and decryption while employing an encryption/decryption algorithm for symmetric purposes36.
Secure network model
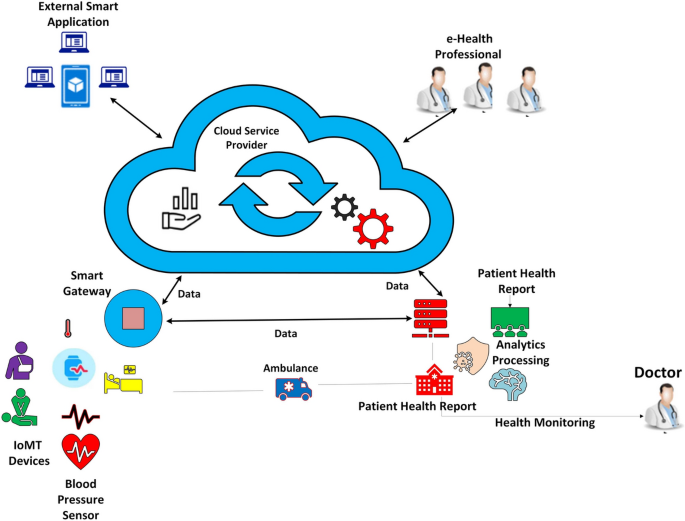
This subsection discusses the various security models used in data security in the cloud-based system. The The security model provides two-channel digital device connectivity to hospitals, merchants, application providers, and doctors. The main duty of the hospital server, which is a reputable third-party server, is to gather and transmit patients, employees, and doctors’ information to merchants. Put differently, this organization determines the information in the patient’s database and responds to the hospital employee with an acceptance or rejection of the patient’s queries37,38. Figure 1 represents the IoMT-based secure netwok model. The information flow in the framework is as follows:
-
The hospital receives requests from patients to provide information digitally.
-
The staff member’s request is sent to the smartphone. Through a wireless connection, the smartphone and the digital devices establish a secure connection.
-
Once a link has been made, the application uses password and biometric authentication to verify patients’ requests for authentication.
-
After the patient’s authentication is successful, information is sent from the wireless device to the employee’s smartphone through hospital applications that have been loaded.
-
Patients initiate and submit requests, such as information portal requests, to any institution.
-
The staff member chooses any patient data and submits the request to the appropriate server, like the staff member’s server, which manages patient communications records.
-
An employee of the hospital verifies the information in their database, validates the patient data, and redirects the exchange of data to the patient’s devices.
-
The hospital database server uses a secure network to confirm patient information and send data to physicians related to specific medical conditions.
-
After completing all verification, the patient’s account is credited with the amount of the payment order.
-
The server will notify the appropriate entities of the patient’s initiator and service provider upon successful validation by the hospital.
Addressing the drawbacks in17 could considerably improve the effectiveness and security in healthcare architecture. The18 refers to a lack of research into advanced or emerging security protocols that could improve protection against new types of cyber threats, whereas the11,13 improves understanding and effectiveness of revocation mechanisms in certificateless public key cryptography, resulting in more robust and practical cryptographic systems. Next,19 aims to improve the creation and use of identity-based signature schemes, resulting in more secure and practical cryptography solutions based on cloud technologies in healthcare settings.
IoMT based secure network model.